



 (11 votes, average: 4.64 out of 5, rated)
(11 votes, average: 4.64 out of 5, rated)On June 8, 2015 the White House Office of Management and Budget (OMB) issued the HTTPS-Only Standard directive, which required that all publicly accessible Federal government websites and services must be served via secure HTTPS connection.
Unencrypted HTTP connections create a vulnerability and expose potentially sensitive information about users of unencrypted Federal websites and services. This data can include browser identity, website content, search terms, and other user-submitted information. To address these concerns, many commercial organizations have already adopted HTTPS-only policies to protect visitors to their websites and services. Today’s action will deliver that same protection to users of Federal websites and services. Click here if you want to learn more about the differences between HTTP and HTTPS.
The HTTPS-only Standard Directive gave federal websites until December 31, 2016 to comply.
Nearly 15 months later, almost 20% of public-facing Federal Government websites still aren’t being served securely.
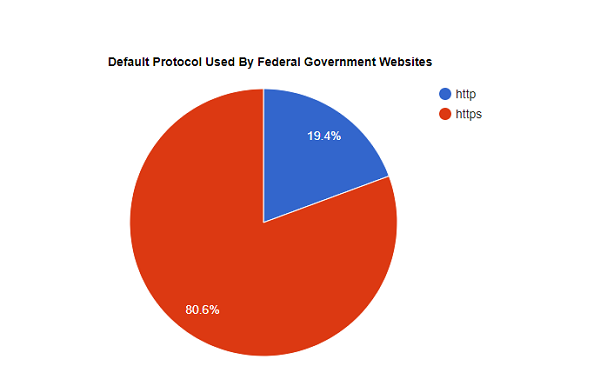
This data is based on checking 1,147 websites operated by Federal government agencies to determine if they serve their homepage over HTTPS by default.
How do federal government websites compare to the top 1,000 websites on the internet? Here’s HTTPS adoption data we collected by checking the top 1,000 sites (ranked by number of monthly visitors in the US):
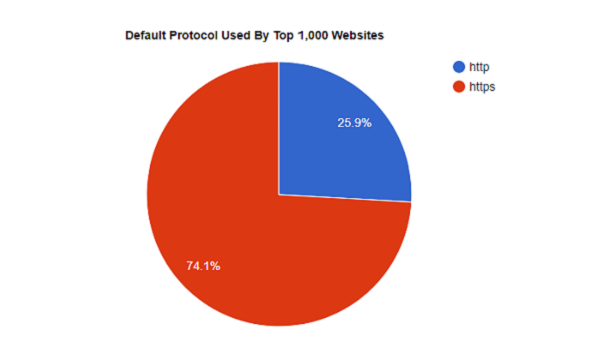
Adoption of HTTPS by Federal government sites is slightly higher than the overall top 1,000 websites in the US.
The unsecure web is built on HTTP, or hypertext transfer protocol, a nearly 20-year-old protocol that facilitates communication between web browsers and the servers that host the websites they visit.
Unfortunately, HTTP is not secure, meaning any data transferred over to protocol is sent in plain-text and can be easily intercepted and stolen or manipulated by anyone with the wherewithal to do so (roughly any middle schooler with an internet connection and YouTube). In technical terminologies, this is called a ‘man-in-the-middle’ attack.
This is why you’re seeing a universal push for websites to install SSL certificates and migrate to HTTPS. An SSL certificate authenticates a web server and facilitates encrypted communication (if you want to dig deep into what these certificates are and what they do, here’s an excellent post for you).
HTTPS only guarantees the integrity of the connection between two systems, not the systems themselves. It is not designed to protect a web server from being hacked or compromised, or to prevent the web service from exposing user information during its normal operation. An HTTPS-only standard, however, will eliminate inconsistent, subjective decision-making regarding which content or browsing activity is sensitive in nature, and create a stronger privacy standard government-wide.
Depending on your outlook on life, the glass is either 80% full or a fifth empty—not to be confused with an empty fifth, which would make telling the difference between HTTP and HTTPS much harder.