Comodo Private PKI
Comprehensive Security Control for Your Enterprise
Comodo Private PKI enables you to create and operate a private certificate authority (CA) for your organization. Issuing your own private certificates protects your internal systems from the outside world and gives you the highest possible level of control over both devices and users. Protect it all, including mobile devices, web servers, IoT devices, DevOps, and cloud applications.
Comodo Private PKI is proven, trusted, and easy-to-deploy. It was created to be a streamlined way for enterprises to enjoy all the benefits of a private CA without the typical headaches and costs associated with their creation:
- Issue all types of private certificates for your enterprise devices
- You don’t have to deploy and manage it yourself
- If you already have a private CA, Comodo Private PKI can manage it while adding new features
- It automatically handles issuing, installing, renewing, and replacing certificates in a fast, scalable, and reliable way
Reduce costs, save time, and make better use of your IT staff, all while protecting your organization from attacks. Thanks to full-featured automation and compliance with industry standards, Comodo Private PKI is the smart choice for your enterprise.
Request More Info
Compliment Your Microsoft CA
Comodo Private PKI was designed with flexibility in mind. It's the most effective solution for company-wide PKI management, regardless of whether you already have an internal CA or not.
Already using Microsoft CA? Comodo Private PKI can augment it. Comodo Private PKI seamlessly integrates with your current Microsoft CA to protect both Windows and non-Windows devices on your networks. Don’t have a private CA yet? You won’t need to create one from scratch yourself—Comodo Private PKI will take care of it all for you.
No matter which route you take, Comodo Private PKI gives you the power to create and run an internal CA without the typical stresses and costs. Comodo Private PKI does the following for you, things that would cost hundreds of thousands of dollars and consume months of labor on your own:
| Creating robust security standards and policies |
Performing backups and keeping them in a safe location |
Providing secure storage for your private CA’s hardware |
Creating and managing the storage of keys and certificates |
| Deploying a secondary backup system in case of an emergency |
Creating a comprehensive disaster recovery plan |
Carrying out audits to maintain ongoing security & compliance |
Creating the root key and documenting the process |
Comprehensive Device & Application Protection
Comodo Private PKI is the most versatile and comprehensive platform for deploying digital certificates throughout your enterprise. It works in harmony with Comodo Certificate Manager to form a cost-effective solution for deploying public or private certificates on your networks:
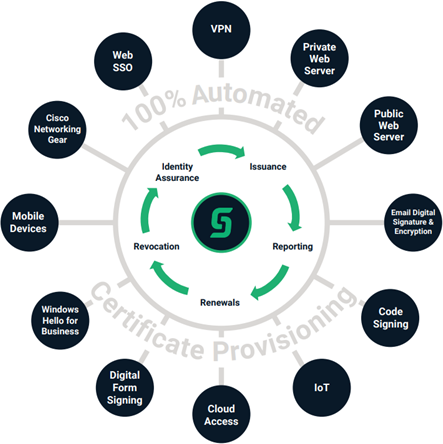
Easily Manage Your Private CA with Comodo Certificate Manager
Comodo Certificate Manager (CCM) removes the load of certificate management from your IT team and transforms it into a fast and easy process. Get an unprecedented level of control over each and every certificate (both public and private) in your company with key features like:

Certificate Discovery
Comprehensive scans find each and every certificate on your networks, no matter what the CA, and performs real-time monitoring. View details like expiration dates and cryptographic ciphers.

Full Lifecycle Management
Automate the installation and renewal of certificates to avoid costly downtime to your business-critical systems. Comprehensive access control lets you revoke in a single click if personnel changes.

Easy Provisioning
Only configure your policies and programs once, then push your settings to all users and devices. CCM supports popular automation standards such as ACME, SCEP, EST, and Microsoft CA’s proxy agent.

Enhanced Reporting
View detailed certificate info on your central dashboard, maximizing visibility and avoiding unpleasant surprises. The critical info you need to make informed decisions is all right there at your fingertips.

Secure Key Storage
Proper protection of private keys is essential, and CCM stores them using the endpoint’s trusted key storage, eg. Windows 10 Trusted Platform Modules (TPM) or Apple’s Secure Enclave.

Custom Access Control
Different team members will have different needs, so give them access accordingly. Granular access controls make it easy to customize access levels exactly how you want, boosting efficiency in the process.

