Data Breach Incident Response – A Complete Checklist
What to do in the first 24 hours and immediately following a data breach
As the internet has evolved, so too has cybercrime. Hackers and criminals are becoming more and more sophisticated with their attacks and in the ways that they exploit vulnerabilities.
Your company or organization may be doing its best to stay on the cutting edge of web security but in this proverbial game of cat and mouse, we’re always just a small advance away from being hacked or having our data breached.
Some of the largest companies in the world have fallen victim to cybercrime, in the process millions of customers’ financial records, healthcare data and personal information has been compromised.
As prevalent as cybercrime is, you may be surprised to discover that, per Protiviti Risk & Business Consulting, one in five organizations do not have a formal incident response plan in place.
With that in mind, we’re providing a checklist of reactionary tasks to help your company or organization formulate its own incident response plan.
What to do in the first 24 hours

Some of these are fairly obvious, others may require a little bit more explanation, but here are 10 steps to take within the first 24 hours of a data breach. Remember, don’t panic. Just keep your head and follow these steps:
- Record the date and time – It’s important to mark down when the breach was discovered and when your company or organization’s official response began. This will aid in the ensuing investigation.
- Alert everyone – If you have a response team this is the time to notify it of the breach. In addition, this is when you should begin executing your preparedness plan.
- Secure the premises – Lock down the physical location where your servers reside in addition to isolating whatever area of your network the breach occurred in.
- Stop exfiltration of data – Take any affected machines offline, but avoid turning them off or interacting with them beyond that—this is a job for a forensics team.
- Document everything – You should keep a running record of every detail, from who discovered the breach and when, to what you know and what steps you’re taking.
- Interview anyone involved – Be sure to talk to (and document your discussions with) whoever found the breach, and anyone else with knowledge of it.
- Review communication protocols – Decide who needs to know what about the breach at this early stage.
- Assess priorities and risks – Take an objective look at what the current risks are and what your top priorities need to be moving forward.
- Bring in a forensic team – You will need to launch a formal investigation into this breach and the forensics team should be the ones leading it.
- Notify law enforcement – First consult with your legal counsel, and then, if necessary, notify the proper law enforcement channels.
Beyond 24 hours
After you have checked the first ten boxes during the initial 24-hour period after the breach occurred, you will need to begin a more in-depth response across a number of other fronts. Here is a summary of five additional tasks that will need to be completed following the breach.
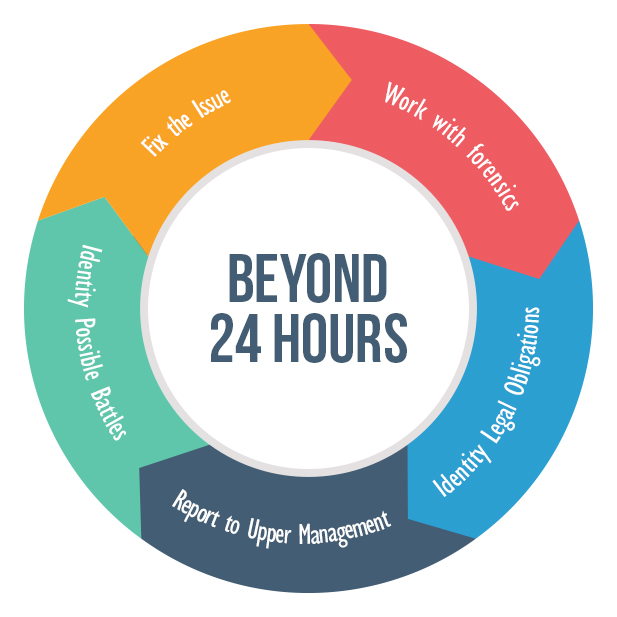
Fix the Issue that Caused the Breach
Your forensics team should have now investigated the network and any affected machines and systems. In the process it will likely have discovered the cause of the breach. Have the team delete any hacker tools and determine if you have any additional vulnerabilities or security gaps. The team should also replace any affected machines with new ones before taking them back online. And make sure to document everything so that you can learn from this situation in the future.
Continue Working with Forensics
In addition to fixing what caused the breach, you’ll need your forensics team to take stock of what exactly was stolen. This means analyzing backup, preserved or reconstructed data sources, figuring out the number of customers or employees that were affected and the type of information that was compromised and then aligning those affected with the stolen data so that you can begin notifying people.
Identity any Legal Obligations You May Have
Once forensics has a full picture of what was compromised and who that affects, have your legal team take a look at any state and federal regulations that govern your industry and the type of data that was lost. Determine who you need to notify and what timetables you have and then ensure that you do actually follow through on those notifications. This isn’t fun, and it’s probably going to hurt consumers’ trust in your company or organization in the meantime. But, not notifying people could lead to even bigger problems.
Report to Upper Management Levels
Chances are that the upper management and executive levels in your company are aware of the breach, but they’re going to want detailed reports on it. You should be keeping them informed of all the facts, including causes, resolutions and potential ramifications. It’s also good to continue to give regular updates as to the progress of investigations and the overall response.
Identify any Potential Conflicts
You’ll need to look at any and all upcoming business initiatives that could potentially interfere with your investigation of and response to the data breach, and make sure both the response team and upper management are aware of them. In some cases, you may need to postpone some things while the response carries on.
In Closing
Remember, investigating and responding to your data breach should take priority over everything else. First and foremost, you need to make sure that you’re secure moving forward. It’s not outside of the realm of possibility that your company or organization could quickly be targeted again, which is why it’s so important to quickly rectify any security gaps or vulnerabilities that could be exploited.
It’s also vital that you investigate the damage and try to find the perpetrators. Until the investigations and response have run their course, you can’t get back to business as usual. And trying to would be a huge mistake.
We hope this checklist will help your company or organization create its own response plan. Remember, this is just a start. Your plan needs to be tailored to your business needs. Do some research, contact security experts and make sure to be proactive about keeping up with web security trends. After all, we’re all just one step away from a major hack or breach.


 (11 votes, average: 4.55 out of 5)
(11 votes, average: 4.55 out of 5)