



 (2 votes, average: 5.00 out of 5, rated)
(2 votes, average: 5.00 out of 5, rated)
When it comes to account security, WordPress salts are critical elements that aid in securing WordPress sites. This is why we’ll begin this article by defining WordPress salts and security keys and identifying their locations within the WordPress framework.
Next, we’ll explore the operational mechanics of these salts and their contribution to user login protection. We’ll also classify the various WordPress salts, highlighting the value of regular updates to these security components.
Finally, we’ll provide step-by-step instructions for updating WordPress salts and keys. This includes covering both manual methods and hints about using WordPress salt generator plugins. This comprehensive guide aims to equip WordPress users with the knowledge and tools necessary for optimal website security.
The trinity of salts, keys, and hashes helps form the foundation of access and password security in WordPress. Salts are applied to passwords before they’re hashed; the resulting hash values are stored in cookies that are used for authentication on the WordPress website. These cookies are encrypted using keys for specific uses to make them more secure against cookie hijacking and other threats.
Not sure what all of that means? No worries — we’ll explore these items more in depth to understand the roles they play in protecting access to your digital domain.
WordPress salts are random data strings that, when combined with passwords, add a layer of complexity to them. In this case, they make stored password hashes more secure and less vulnerable to brute force attacks. This is critical in an era where brute force-related data breaches are major concerns for businesses and consumers.
According to WordPress Developer Resources, salts are created using secret keys that are randomly generated and stored in your database and wp-config.php file. The key stored in your database is dynamic, meaning that it’s randomly generated. The one stored in your wp-config.php file is one you should manually update with some regularity — WP Engine recommends doing so approximately once a month or every quarter.
WordPress employs salts to protect password data — a fundamental yet often overlooked strategy. To illustrate, consider salts as unique modifications to each WordPress “lock” combination. Envision your password as the combination that secures a safe. The salt is like an additional sequence of numbers added to your combination that is unique to your lock. Even if others have a similar combination, without the exact additional sequence — i.e., the precise way the specific salt was added — their attempts will fail to open your safe.
Again, for an everyday comparison, consider a salt like a secret spice you’e used when cooking a meal. Even if someone has the general list of ingredients, without that secret spice (and its specific measurement), they can’t quite recreate the original recipe’s unique flavor. Similarly, cryptographic salts ensure that your WordPress password — no matter how simple it may be — is altered into a unique code that provides a sturdy barrier between your data being safe or exposed in a security breach.
Salts are crucial to password security because they decrease the likelihood of hash collisions (i.e., generating the same password hash value). They make it so that even if two people are using the same password, their resulting hash values are different because the salts have been added to them before hashing.
This approach makes it hard for bad guys to use the hash values in brute force attacks. As such, trying to launch cyber attacks using pre-computed rainbow tables would be too infeasible for bad guys to carry out because of the amount of time, work, complexity, and costs involved.
In the context of WordPress security, the terms “keys” and “salts” are often used interchangeably because they work together to secure your site. However, security keys serve related but distinct purposes. They make the data used in cookies more complex and harder to guess, contributing further to session security.
To further clarify, salts and keys are crucial for security, but they have distinct roles. Salts are primarily used to secure passwords by creating unique hashes, whereas keys are involved in encrypting session data like cookies. This differentiation is important to understand the full scope of WordPress security measures.
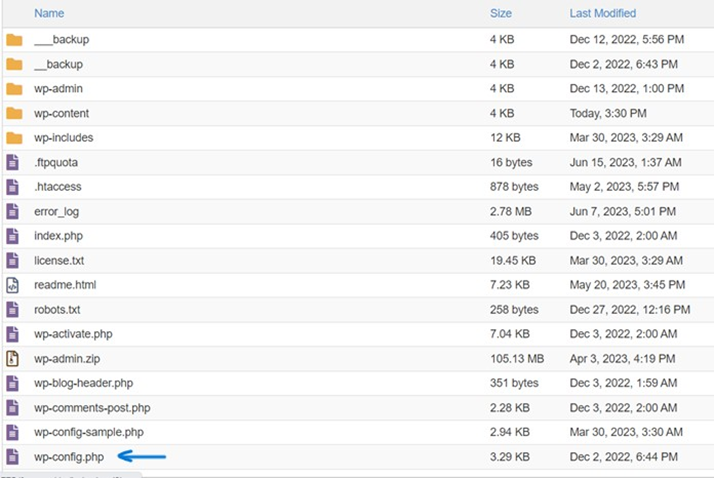
The heart of WordPress salts lies in the wp-config.php file. This isn’t just any file; it’s the backbone of a WordPress installation, housing critical settings that govern the site’s operation. Located in the root directory of a WordPress installation, this file holds the key to your database’s connections, unique authentication keys, and of course, the salts themselves.
If you open wp-config.php, you’ll find the salts and keys neatly lined up as definitions. They look something like this:
define(‘AUTH_KEY’, ‘Enter your unique phrase here’);
define(‘SECURE_AUTH_KEY’, ‘Enter your unique phrase here’);
define(‘LOGGED_IN_KEY’, ‘Enter your unique phrase here’);
define(‘NONCE_KEY’, ‘Enter your unique phrase here’);
define(‘AUTH_SALT’, ‘Enter your unique phrase here’);
define(‘SECURE_AUTH_SALT’, ‘Enter your unique phrase here’);
define(‘LOGGED_IN_SALT’, ‘Enter your unique phrase here’);
define(‘NONCE_SALT’, ‘Enter your unique phrase here’);
Each line denotes a specific salt or key. WordPress uses these salts to add extra security layers to the passwords and tokens used on your site. Each instance of the phrase “put your unique phrase here” (as seen above) is a placeholder, meant to be replaced with unique values (which will be discussed further in the article).
Here’s an example of WordPress’s salts, as published in its website salt generator tool:
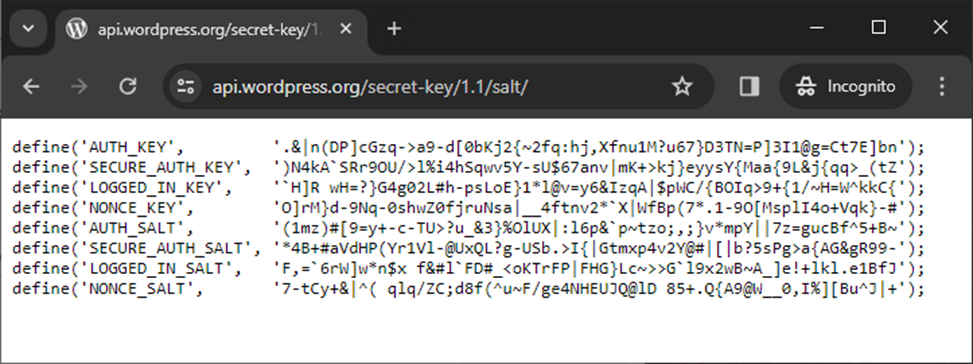
It’s important to note that changing your keys and salts in the wp-config.php file will log all users out of their accounts and require them to sign back in again. While this may be an annoyance from a user’s perspective, it’s a small price to pay for greater account security.
Hashing is the process of taking an input (e.g., a password) and applying a cryptographic formula to it that generates a unique, fixed-length output (e.g., a password hash value).
When a WordPress user sets a password, the system augments it with a salt automatically before it goes through the hashing process. The resulting hash is a scrambled string of characters that’s stored in place of the actual password. (This is because storing passwords in plaintext is a big faux pas in the security world!)
$hash = password_hash(‘user_password’, PASSWORD_DEFAULT);
The above example password_hash function generates the following output in WordPress:
$2y$10$eCRc1Kf3.FVQ8b2jyR/3seI9NDP3zB9qgS2N5uhjZmFP5pNKy3DaS
Generally speaking, when you add unique salts to passwords, even if two users use identical passwords, their hashes will be different. Doing this improves security by making it harder for attackers to gain unauthorized entry to user accounts. While the method of password salting might appear simple, its significance for security is profound. Each password hash, altered by a unique salt, acts as a guardian against unauthorized access, including brute force attacks and rainbow table attacks.
WordPress improves its security architecture through the strategic use of four unique salts, each targeting a different aspect of user data and session security:
By employing these distinct salts, WordPress creates a multi-layered security system. Each salt has a specific role, collectively making it far more challenging for unauthorized parties to access sensitive information. This approach shows WordPress’s commitment to providing comprehensive and nuanced protection for user data and session information.
In addition to these salts, WordPress also utilizes corresponding security keys — AUTH_KEY, SECURE_AUTH_KEY, LOGGED_IN_KEY, and NONCE_KEY — which, generally speaking, work in tandem with the salts to further strengthen the security of user data and sessions.
Regularly updating WordPress salts isn’t just good practice; it’s a cornerstone of proactive WordPress website security. All user sessions are reset by changing these salts, which is particularly important after a security breach. This process invalidates existing cookies, which means that users will need to log in again to re-authenticate.
Why is this important? In the event of a website compromise, attackers may gain access to user cookies, which can then be used to impersonate legitimate users. Updating and changing WordPress salts makes previously valid cookies obsolete, cutting off unauthorized access. This is particularly required in scenarios where a website has been hacked.
Regularly replacing the salts with new, random values as part of the response plan confirms that attackers cannot continue to exploit the previously stolen cookies. In essence, changing WordPress salts is akin to changing locks after a break-in. It’s a straightforward yet effective measure to resecure a site post-compromise, safeguarding both user accounts and the overall integrity of the website.
This practice is an essential part of a comprehensive security strategy that helps maintain the trust and safety of a WordPress site. Additionally, updating the keys periodically helps to ensure you’re using the most secure keys possible, adding another layer of defense against potential security threats.
So, in practical terms, updating salts and keys means reinforcing the barriers that keep unauthorized users out of your WordPress site. For a site administrator, this translates to greater confidence in the site’s security, especially after a security incident. For users, it means their data remains secure, even in the face of evolving cyber threats.
Of course, you shouldn’t wait for your website’s user accounts or sessions to be compromised to make these changes. Rather, change your WordPress salts regularly to help avoid potential future compromises.
Updating WordPress salts is a simple process, achievable through two primary methods: manual updating and using plugins.
This method involves direct interaction with the wp-config.php file located in the root directory of your WordPress installation.
// Security Keys and Salts
define(‘AUTH_KEY’, ‘example_key’);
define(‘SECURE_AUTH_KEY’, ‘example_key’);
define(‘LOGGED_IN_KEY’, ‘example_key’);
define(‘NONCE_KEY’, ‘example_key’);
define(‘AUTH_SALT’, ‘example_salt’);
define(‘SECURE_AUTH_SALT’, ‘example_salt’);
define(‘LOGGED_IN_SALT’, ‘example_salt’);
define(‘NONCE_SALT’, ‘example_salt’);
// Customized Security Keys and Salts
define(‘AUTH_KEY’, ‘B8g*F^J6h2K@Lz!3+9sA’);
define(‘SECURE_AUTH_KEY’, ‘p]G3tR8x^P&6W>q@L#-m’);
define(‘LOGGED_IN_KEY’, ‘E7@N2#4s5Dy?C&+Pz]4x’);
define(‘NONCE_KEY’, ‘kM8^4s+J&y8P:9D*LzY>’);
define(‘AUTH_SALT’, ‘N6S^9b4!8w&J3@J9zE*2’);
define(‘SECURE_AUTH_SALT’, ‘Mw5?4K8z$+3x@V9Jb#<+’);
define(‘LOGGED_IN_SALT’, ‘L9rC*5;2S/G6F8Y&Wt?A’);
define(‘NONCE_SALT’, ‘7zE9P&D8Y@F6^J3+H2Wk’);
Remember, the above strings are just examples. Generate your own unique values for security.
This process increases your WordPress site’s security by refreshing its cryptographic security mechanisms, guaranteeing that your user data remains protected.
Updating WordPress salts and keys using a WordPress plugin such as Salt Shaker is helpful for those who prefer not to edit files directly. A plugin like this allows you to change the salt keys either manually or automatically, enhancing the security of your WordPress site.
Here’s how you can use the Salt Shaker plugin for this purpose:
Installation:

Configuration:
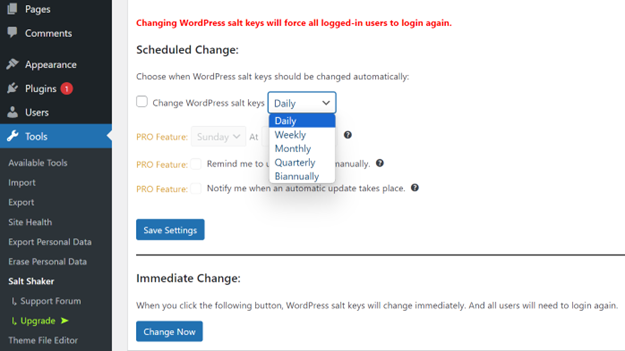
These steps will help you manage and update your WordPress salts, providing high security without editing critical files.
The prominence of broken access control in the OWASP Top 10 is a compelling reminder of the importance of robust access security measures. It climbed to the top position in 2021, underscoring a widespread challenge: 94% of applications were tested for vulnerabilities related to improper access controls, more than any other category.
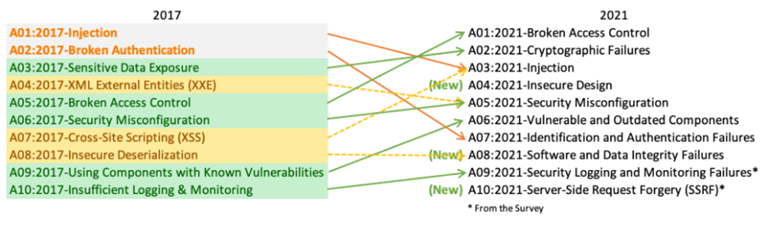
This statistic from the OWASP Top Ten highlights why WordPress users must prioritize their website’s access security. Implementing strong security measures, including the use of WordPress salts to secure password data, is not just advised; it’s imperative in the face of the prevalent risk of access control breaches.
For WordPress site administrators, understanding and applying such security protocols is essential to protecting against the most common and impactful security risks outlined by experts by OWASP.
If you are looking for comprehensive security of your website, it is always wiser to integrate a robust security service like SiteLock with your WordPress platform. The benefits of WordPress salts and keys only extend so far. SiteLock provides a broader range of protective features that can help protect your website against many website security threats.
Here are some essential aspects of SiteLock that can develop an overall WordPress website security:
SiteLock’s approach to website security, with real-time updates and a diverse array of protective measures, makes it a strong choice for improving WordPress website security. It’s about creating a resilient environment that actively combats a spectrum of digital threats.

Strengthen Your WordPress Security Against SQL Injection Threats with SiteLock
Protect your WordPress site and web apps against SQL injection threats with SiteLock’s advanced, comprehensive security tools.
Maintaining updated WordPress salts is an essential yet often overlooked aspect of password security for WordPress website owners. This practice plays a pivotal role in fortifying the site’s security framework. Regularly refreshing these salts, either manually or via reliable plugins, helps to ensure that user data remains encrypted and less susceptible to unauthorized access.
The above action, especially when combined with SiteLock and other security mechanisms, builds robust defenses for your website, benefiting both users and administrators. In summary, treating WordPress salts as a dynamic and integral part of your site’s security strategy is inevitable for a safer online experience.