



 (7 votes, average: 5.00 out of 5)
(7 votes, average: 5.00 out of 5)Certificate Transparency is a Google initiative aimed at increasing the safety of the SSL/TLS Certificate System. Namely, Certificate Transparency has been put in place to defend against mis-issuance.
This is an extremely important safeguard for the SSL/TLS ecosystem. It’s absolutely vital that when a Certificate Authority issues an SSL Certificate, that it issues that certificate to the correct party. Think about it, a large company like PayPal requires an SSL Certificate for both encryption and authentication. It’s obviously very important that a company that deals in financial transactions be able to encrypt communication. But it’s equally important that PayPal be authenticated so customers have assurance they’re dealing with the actual company and not an imposter.
So, you can probably imagine, if a CA were to mis-issue an SSL Certificate to a company that wasn’t PayPal—all hell would break loose.
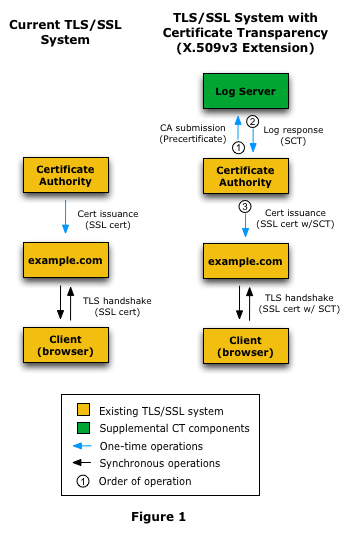
This is why Google has pushed for Certificate Transparency, which essentially requires CAs to log all certificates they issue in publicly accessible Qualified CT logs.
Let’s take a look at how it works:
There are four main participants in Certificate Transparency. They are:
The following occurs when a CA logs a certificate:
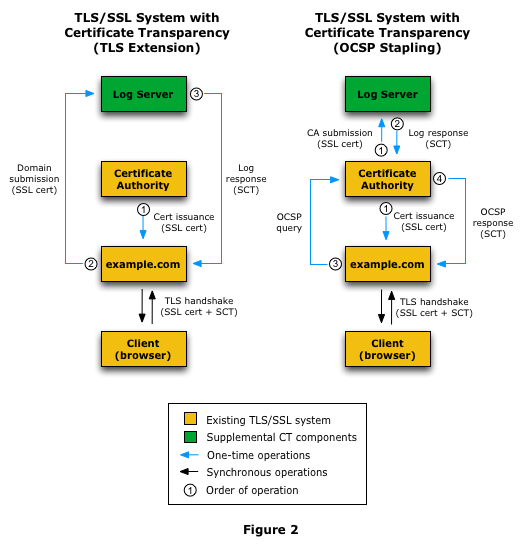
There are three ways for an SCT to be delivered with the SSL Certificate:
For obvious reasons, publicly logging SSL Certificates carries a great number of advantages for both CAs, browsers and end users.
From the standpoint of the CA, logging issued certificates requires just a single extra step, but allows them to cover themselves should a mistake be made and a certificate require revocation. In the past it would have taken much longer to discover a mis-issuance or mistake and then the CA would have to act quickly to revoke the certificate. This cuts down on the time it takes to discover bad certs and allows the CAs to act much more quickly.
It also allows browsers and end users to check the validity of issued certificates much more quickly. Soon, Google Chrome will actively block connections to websites with SSL Certificates that don’t also have SCTs. This will help to keep end users safer and will force websites to use SSL from trusted CAs. Overall it will help to make the internet more secure.
There’s really no downside to Certificate Transparency if you’re acting in good faith. It helps CAs, browsers and end users by creating a great degree of accountability and by ensuring that bad certificates can be revoked more quickly.
Images Source: https://www.certificate-transparency.org/