How to Fix a Hacked WordPress Site: A Step-by-Step (DIY) Guide
A 2022 WordPress security survey shared that about 43% of admins spend up to three hours each month on security measures, often focusing on fixing hacked sites. Are you in a similar situation? Here are eight steps you can take to regain control and secure your website against future attacks.
As a leading encryption provider, we often receive inquiries from individuals and businesses dealing with hacked WordPress sites. They frequently ask, “My WordPress site has been hacked. What should I do?”
Invariably, the first step for how to fix a hacked WordPress website is not to panic. Considering that a hacked WordPress site can have serious consequences, we know that’s easier said than done. These negative impacts include a drop in search engine rankings, potential exposure of visitors to harmful viruses, damage to your reputation, and even loss (or theft) of sensitive site data.
Take a deep breath and read on to learn how to kick that hack to the curb!
How to Fix Your Hacked WordPress Site in 8 Steps
Every day, Colorlib estimates there are more than 13,000 cyber attacks on WordPress websites, totaling more than 4.7 million annually! Keep your WordPress website from being the next target. Protect yourself from the threats lurking on the web.
If you suspect your WordPress site has been hacked, there are ideally three critical phases to fix the issue:
- Identify the hack and determine the extent of the damage.
- Clean up the hack and remove any malicious code or files.
- Carry out post-hacking measures, like implementing WordPress hardening to prevent vulnerabilities and future hacks, are essential.
With this in mind, let’s explore the eight steps you can take to remedy the situation when you realize “my WordPress site is hacked.”
Step 1: Put Your WordPress Site in Maintenance Mode
Picture this: you wake up one morning, ready to check on your website, only to find that it’s been hacked! Panic sets in. The best thing to do is to stop and take a deep breath.
First and foremost, don’t let a compromised website ruin your reputation! Instead, enter maintenance mode to protect your visitors and brand.
With a WordPress plugin, you can quickly activate a message letting visitors know your site is undergoing scheduled maintenance rather than being hacked. Customize the “Maintenance mode” message with your logo and brand colors to maintain credibility.
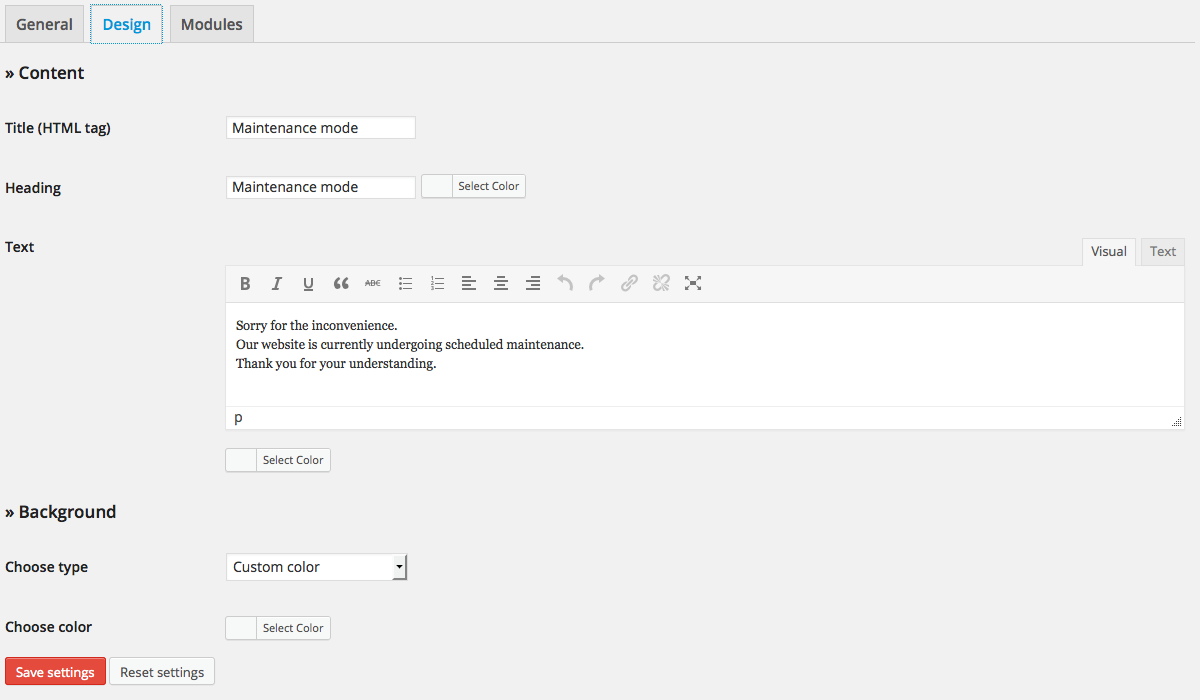
Even if you can’t log in immediately, activate maintenance mode to prevent further damage and protect your website and reputation.
Step 2: Assess the Hack Severity
When dealing with a potential website hack, it’s important first to identify the attack and determine its severity. To do this, ask yourself five critical questions while navigating the affected site.
- Can you log in to your WordPress panel?
- Is your site showing as secure on Google Transparency Report, and has it been affected by any traffic issues?
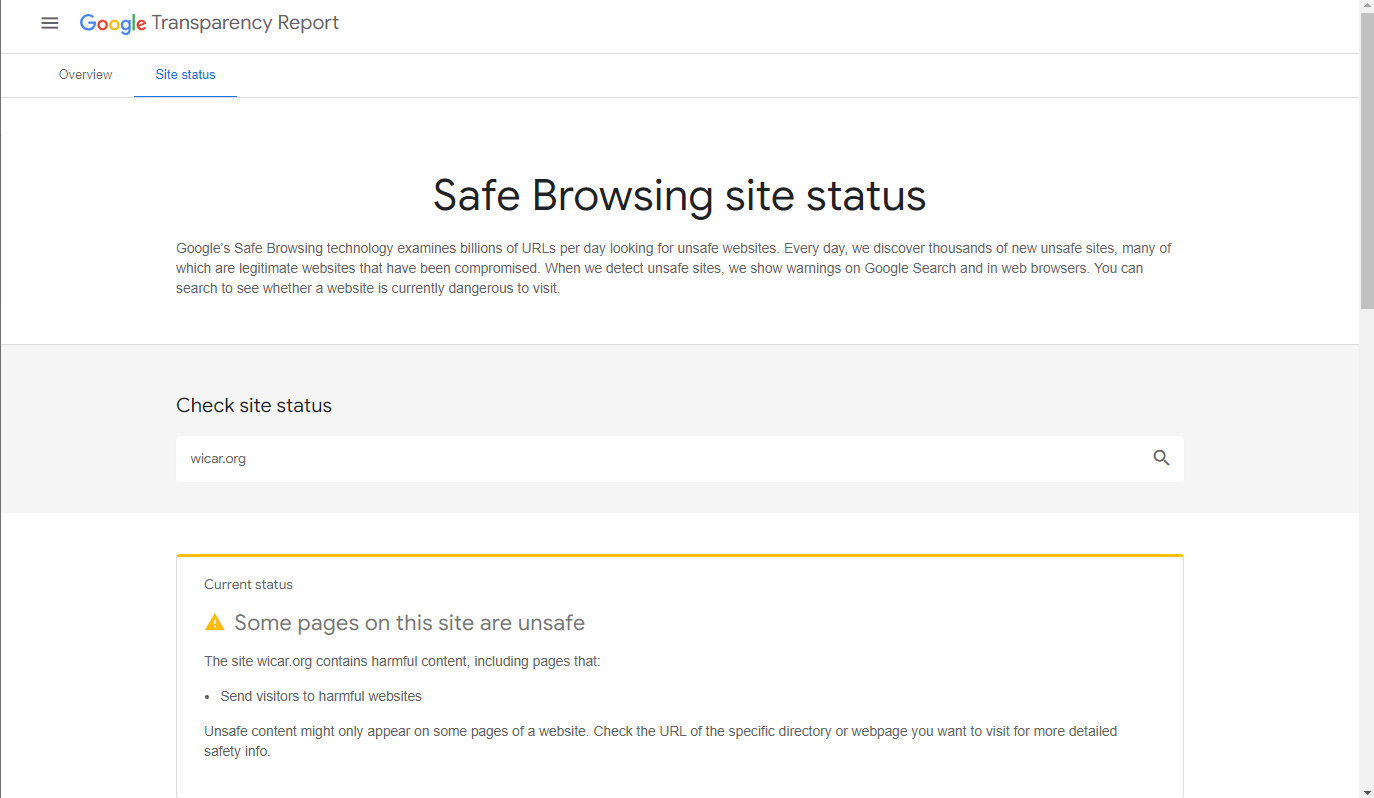
- Is your WordPress site hacked and redirected?
- Is your home page defaced and vandalized with a ransomware threat?
- Do you notice any illegitimate links or unwanted popup ads on your website?
Run the above checks to determine the extent of malware infections on your WordPress site. The Google scan report will swiftly pinpoint any malware infections that may be causing spam, malicious downloads, or redirects. Please take note of the answers to these questions to help identify the hack or explain it to others.
Step 3: Change Passwords Before AND After Site Cleanup (So, Do It Now AND Later)
It’s important to change your passwords before you start cleaning up any potential hacks. And we’re not just talking about your WordPress login — you’ll also need to reset passwords for all admin users, your SFTP, your database, and even your hosting provider. Why? So don’t allow the hacker to strike again mid-process; take control of your security.
Of course, to be on the safe side, you also should change all your passwords again after finishing the cleanup. This way, if the temporary passwords were compromised before you successfully removed all malware or malicious code from your site, the temp passwords can’t be used against you once you’ve removed all of the malware. (I.e., this way, bad guys can’t go back in after the fact and insert malware or malicious code all over again.)
Step 4: Remove Malware: Clean Up the Hack
Once you’ve confirmed a hack on your WordPress website, it’s time to act and clean it. First, we suggest you run a WordPress security plugin to determine which files have been altered. Then, once you have the infected file report, go over the steps for manually cleaning a hacked WordPress site.
If you can’t access the WordPress dashboard, use SSH or Linux terminal commands to check the files manually.
Check for Modified Core WordPress Files:
Perform an integrity check on three core folders: wp-includes directory, wp-admin, and root folders.
- Use the SiteLock plugin to scan the core files and see if any changes have been made.
- If changes are found, replace the modified files with your backup’s fresh (unmodified) copies from your backup.
- Again, look for any modifications; if none exist, your core files are clean.
(Note: Handle core files carefully to avoid overwriting wp-content or wp-config.php.)
Check for Modified Themes and Plugins:
While examining modified themes and plugins within the /uploads/ directory, you must be cautious about preserving any custom code changes you’ve made to your theme. Follow these steps:
- Identify modified themes and plugins. Review themes and plugins in /uploads/ for altered files.
- Replace all corrupted files. If you find corrupted files, replace them with fresh versions from the original publisher or developer. (Keep in mind what we address in the next bullet point.) This ensures your site’s functionality is restored.
- Protect custom code changes. Remember not to overwrite any personalized theme code modifications you’ve added. Overwriting files could result in the loss of these customizations.
It’s essential to note that if you’ve integrated custom codes or modifications into the files you’re replacing, you risk losing these tailored elements. Proceed carefully when replacing files, especially if personalized code enhancements are present.
The Power of Backups for Custom File Security
Custom files are crucial to the functionality of your WordPress site, but they can also be vulnerable to malware and other threats. That’s why it’s essential to have recent backups should any changes be detected. SiteLock is a tool that automatically performs daily backup updates for your website’s database and files.
Backing up your custom WordPress files is crucial for site security, but relying on one backup is insufficient. Consider creating multiple copies in different formats and storing them in diverse geographic locations to enhance your plan. Adhere to the “3-2-1 backup rule” for added protection. A comprehensive backup plan ensures your site’s valuable data is well-protected and resilient in any crisis.
Not having a backup means you’ll have to manually scan your files for suspicious activity and delete them to eliminate any threats. This can be time-consuming and add to your workload, as you’ll also need to recreate any lost files. Stay tuned as we discuss more about the WordPress backups later in the article.
Check Database Tables for Malware:
After WordPress installation cleanups, it’s time to clean up your database. However, scanning malware in the database manually is a time-consuming process. So, instead, use a WordPress database plugin to scan any malicious code and unfamiliar records, then clean the database manually.
To manually remove the malware:
- Access the admin panel, connect to your database,
- Scan for suspicious content,
- Remove any infected pieces, and
- Test your website after cleaning.
With the above steps, you mitigate the risk of backdoors created through a database injection!
Later in the article, we’ll discuss why hackers create backdoor malware to bypass authentication in WordPress files.
Step 5: Identify Unknown Accounts and Verify Permissions
To keep your WordPress website from falling into the wrong hands, be diligent about who has access to the admin dashboard. Take a quick peek at the users’ section and limit administrator access to secure access to your WordPress site.
Hackers love to create sneaky entrances into your website, and one of their favorite tricks is to create unauthorized privileged user accounts in your WordPress admin area. These accounts give them access to your site even after you’ve cleaned up any malware. So, stay diligent and watch for any new admin accounts you or your team need to recognize. If you spot any, delete them ASAP to keep your site safe and secure.
When managing your WordPress platform, limiting the number of privileged users is important. Instead, focus on assigning essential user roles like author, editor, and contributor based on what access each user needs to do their job. By doing this, you can ensure that only those who need access to certain features have it, keeping your site secure and organized.
Step 6: Detect and Eliminate Backdoor Vulnerabilities
Hackers employ clever techniques to sneak into websites, including leaving hidden backdoors.
A backdoor is a secret route that hackers exploit to access your website without detection. These access points are designed to imitate essential site files like wp-config.php and critical directories such as /uploads, /themes, and /plugins. They are deliberately positioned in incorrect directories, making them more challenging to identify.
For example, hackers can access and manipulate server content undetected in a WordPress installation by disguising these files with unsuspecting names, like WordPress’s xml-rpc.php. (This file enables remote connections to WordPress and can be used to create backdoors.)
To uncover these covert backdoors, look for recently modified files (already discussed earlier in the article). In addition, you can find hidden pathways hackers use to compromise website security by identifying suspicious changes.
Prevent hackers from sneaking into your system repeatedly, understand backdoors, and use PHP function recognition to detect them.
Step 7: Essential Post-Hack Hardening Steps
Even though you’ve fixed the WordPress site hack, don’t let your guard down yet. There are additional measures to take to prevent another attack from happening. Keep your site safe and secure with these post-hack tips.
- Regularly update WordPress. Keep your WordPress site safe from hackers by regularly updating your core files, plugins, and themes. Safeguard against hacks by staying current with security patches.
- Change your security keys. Keep your WordPress site secure with security keys and salts — generate a new one for each and add it to your wp-config.php file to prevent hacking and give yourself a fresh start.
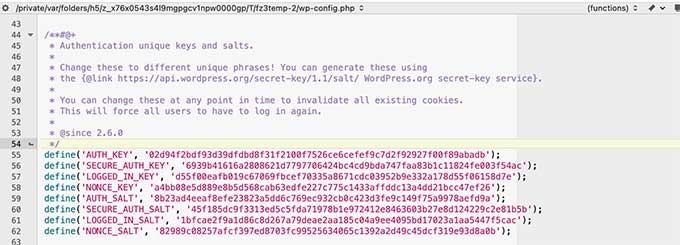
- Scan your local devices. Don’t overlook the risk that your local computer (or the devices of other authorized users) might get infected. Protect yourself against keyboard logging malware and potential data leaks, and scan with an antivirus program.
- Install a robust security plugin. A security plugin alerts you to changes made in real time and scans for malware to keep your site safe from malicious attacks.
- Install a strong web application firewall. A robust firewall protects your website from external threats. It blocks attacks before they reach your server and reduces the chances of hacks and DDoS attacks.
Step 8: Banish Malware Warnings to Reclaim Your Clean WordPress Site
After battling a hack, it’s crucial to eliminate those pesky malware warnings. When your site gets infected, it often lands on blocklists maintained by antivirus software (Symantec, McAfee, etc.) and search engines (Google, Mozilla, etc.).
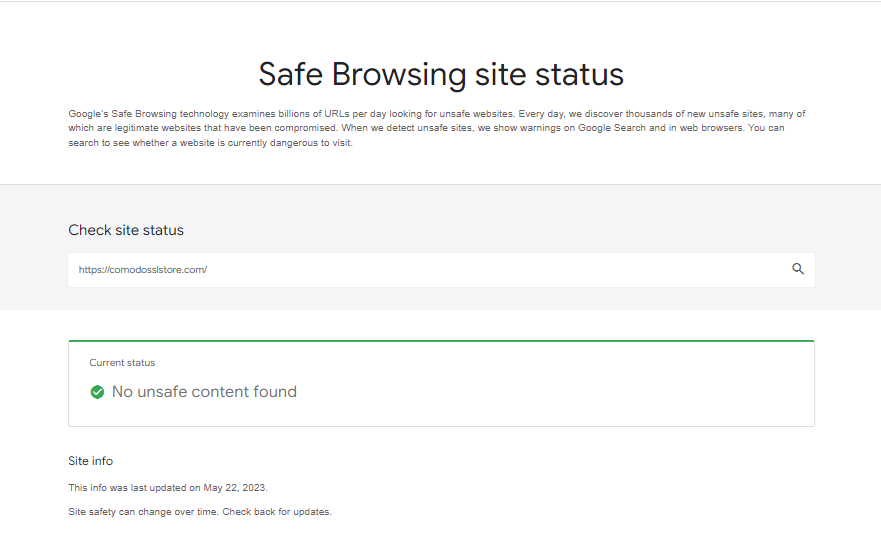
To regain your site’s reputation, it’s crucial to eliminate these warnings. Once you’re confident your site is clean, request a review from the software and browser authorities to restore its trustworthiness. You can request this type of review through Google Search Console, for example. The process for this varies depending on the nature of the hack, but it’s critical to safeguard your site’s integrity to ensure it is no longer flagged as a security risk.
Final Thoughts on Fixing a Hacked WordPress Site
Hackers search for vulnerabilities in WordPress sites to inject malware and steal data, causing harm to the site and visitors. Of course, nobody wants their website hacked, but if it happens, we have just discussed several remediation methods you can use to fix the situation.
For WordPress beginners or those lacking technical expertise, seeking professional services is a wise choice. With various providers offering urgent plans, you can have your site back up and running within hours.
Alternatively, if you prefer a do-it-yourself (DIY) approach or have budget constraints, this comprehensive guide provides step-by-step instructions to fix hacked WordPress sites. Alongside this DIY guide, opt for advanced WordPress defense services like SiteLock that empower you to safeguard your site and regain control over its security.

Don’t let malware compromise your WordPress site. Instead, take prompt action, and ensure your website remains protected against future threats.



