What is Ransomware? 5 Straightforward Steps to Protect Against it
Steer clear of ransomware attacks by implementing our experts’ instructions
If you have been keeping up with the latest technology news, or any news for that matter, you would at least have heard of the ‘WannaCry’ ransomware attack. This attack hit globally and left countless people as well as many security experts in limbo. WannaCry malware, also known as WannaCrypt spread rampantly across the world paralyzing hundreds of thousands of systems of more than 150 countries.
While the WannaCry ransomware attack has slowed down for now, unfortunately, it is not the only malware out there. With notorious ransomware of 2016/17 such as Locky, Cerber, CryptoWall, CryLocker, TeslaCrypt and EternalRocks still floating around, danger is still looming large. Therefore, it is absolutely critical to understand the very nature of ransomware attacks and to take substantial actions to prevent them.
What is Ransomware?
Imagine not being able to access your own information/data on your own computer and having to pay to get it back. That is exactly what a ransomware attack does. That’s actually half of the business model for the tow truck industry – and we just kind of accept it – but don’t you dare touch our precious computers! Essentially, a ransomware attack locks you out of your computer by encrypting all the data on it using a private key that only the hacker has access to. Consequently, not allowing you to access your own data until you pay a ransom—usually in bitcoin. The victims often fall for it in the fear of their data being published online or getting deleted.
Ransomware attacks have been around for quite some time, but lately attackers have become much more sophisticated when it comes to creating and circulating ransom cryptware, the file responsible for encrypting all the information.
Primarily there are two types of ransomware malware, namely encryptors and lockers. Encryptors, by means of malicious software also known as malware, encrypt all the files on a PC or network. Lockers, on the other hand, lock the entire operating system, thereby making everything inaccessible. Contrary to widespread belief, ransomware attacks are not limited to desktop or laptop computers. Mobile phones can feel its wrath, too.
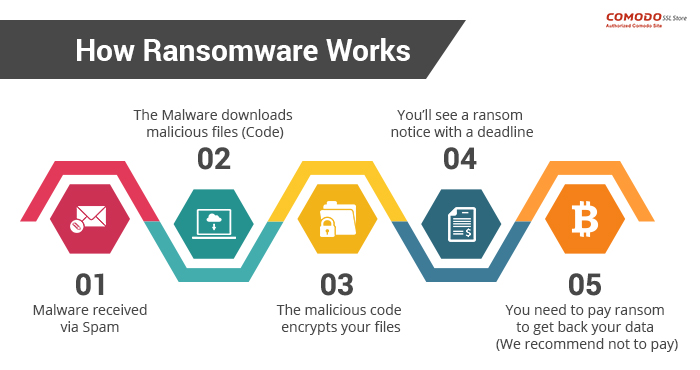
How does it work?
There are two ways one can become the victim of ransomware. The first one involves the intervention of the user him/herself. This method of ransomware requires a user to click on a suspicious link or download a mischievous file(s). It often comes as an email. Upon clicking the link or downloading the attachment, a downloading file is implanted on the device. This downloader file then contacts the domains & servers which are controlled by the perpetrators behind the attack and requests the server to download the ransomware file(s). The C&C servers send the ransomware program. The downloaded malware file(s) then encrypts everything, including the data present on connected devices.
On the other hand, the second method doesn’t even require the user to click anywhere or download anything. The threat can emerge from a vulnerability already present in the software installed which works the same way.
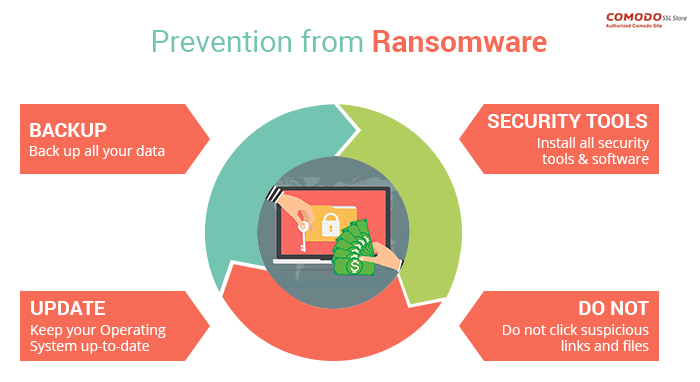
How to protect your systems against ransomware
If we were all a part of a utopian dream, then all the agencies, governments, tech companies and corporations would take a hardline approach to stopping future ransomware attacks and there would be no attacks anymore. But sadly, this is not the case. There will be ransomware attacks in the future and you are the one who must take precaution measures to make sure that you are not the next ransomware victim. Here are our recommended actions for to help you defend yourself:
1. Back up all your data
Backing up your data is the most crucial action in the pursuit of preventing ransomware attacks on your system. There won’t be many reasons to worry if you have your data backed up in another system. One thing to note here is that ransomware programs not only lock up all the data present in the main system, it also encrypts information existing on USB drives as well as on the network or cloud stores. So, make sure that the device used to backup is disconnected once the backup is carried out.
We suggest doing this on regular basis and making it a requirement for all employees.
2. Keep your operating system up-to-date
Not many people know that Microsoft released a patch back in March that could have protected recent versions of Windows against WannaCry. As reported by BBC, systems running on Windows 7 were found to have been affected the most by WannaCry. This could have been easily prevented had the users been a bit cautious and updated their devices. Now, those unlucky victims have only themselves to blame.
Therefore, whenever you see an OS update, do it ASAP.
3. Use proper security tools
Although you may be tired of hearing it (or in this case, reading it), we will say it one more time. Install anti-virus software. Having anti-virus software installed can help in preventing ransomware attacks by keeping malware at bay and warning users before visiting any vicious site. We also suggest using a strong firewall and bolstering it by adding an anti-ransomware tool.
4. Avoid suspicious links and files
Here are the best practices to steer clear of a ransomware attack:
- DO NOT open a suspicious looking email, especially if it is from an unknown sender
- Download files from the trusted sources only
- Keep optimizing your email spam folder
- In case of slightest of doubts, contact your company’s IT department
- Be cautious before clicking any site while surfing
5. Disable Windows Script Host and Windows PowerShell
For Windows users, we strongly recommend disabling Windows programs such as Windows Script Host and Windows PowerShell as it restricts the malware from infecting and spreading in the system. Windows PowerShell allows programs and tasks to run without administrator’s permission; which is exactly what the cyber criminals are looking for. Therefore, disable them right away.
Ransomware—to pay or not?
Ransomware works the same way as an actual kidnapping works. In the case of kidnapping, the police will tell you not to pay the ransom no matter what. Here too, we strongly advise you not to pay the ransom as there is no guarantee that you will get your data back. Moreover, it encourages the attackers to attack more systems in the future.
Final Thoughts
According to the recent report published by security firm Kaspersky, it has been reported that there has been mammoth 250% rise in ransomware attacks this year. Therefore, the need to protect against it is now more than ever. Although, there is no guarantee that you will stay clear of any ransomware attack by implementing the aforementioned measures but it is always good to stay a step ahead, don’t you think?


 (7 votes, average: 4.43 out of 5)
(7 votes, average: 4.43 out of 5)