How to Check If Your WordPress Site Has Been Hacked: A Comprehensive Checklist
Web security is a pressing concern as approximately 30,000 websites are hacked daily, with more than 43% of websites use WordPress as its content management system (CMS).
As a web security company, clients often ask us how to check if your WordPress site has been hacked. As a business or website owner, you must be aware of the potential hacking risks on your WordPress site. But, detecting whether your site has been hacked can be a challenge.
Watch for signs of hacking on your website, such as strange activity, redirects, or setting changes. Act quickly if your WordPress site is hacked, and look for potential red flags, as mentioned in this article.
We’ve compiled a comprehensive checklist to address your concerns on how to tell if your WordPress site has been hacked.
10 Warning Signs Your WordPress Site May Have Been Hacked
The number of cybercriminals infiltrating networks with different types of malware is increasing, making it a complex and costly threat to corporations worldwide. According to Cisco’s Cybersecurity Threat Trends Report, their skills and danger continue to rise, emphasizing the need to stay vigilant and take action at the first sign of a compromise.
To help you detect potential security breaches on your WordPress site, we have compiled a step-by-step checklist of red flags to look out for.
For most website owners, handling security warnings, hack indicators, and diagnostic pages can be overwhelming and intimidating. To prevent potential security breaches on your WordPress site, it’s best to be proactive and keep this detailed guide handy to identify the warning signs.
1. Google Lists the Site as Unsafe, or You See a Significant Drop in Traffic
If your Google Analytics dashboard suggests a sudden decrease in traffic on your WordPress site, it’s reason for concern as it may indicate that your website has been hacked. This can happen for various reasons, such as malware on your website that redirects non-logged-in visitors to spam websites or Google’s Safe Browsing tool warning users about your website.
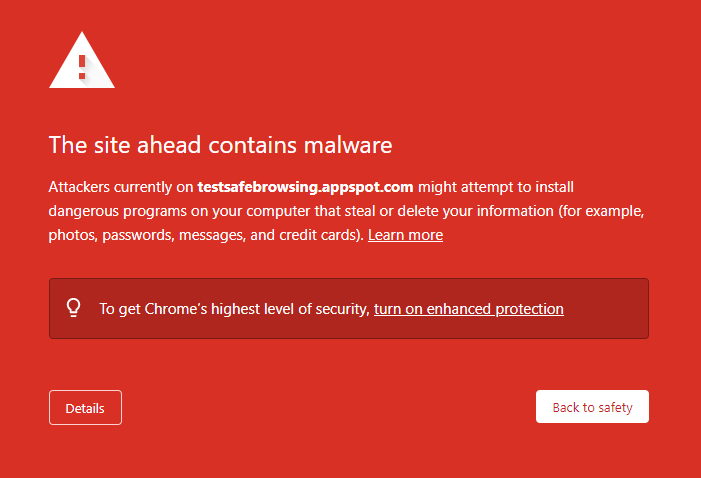
This hack is often challenging to detect because it doesn’t affect users who are already logged in or access the site directly by typing the address into their browser. You’ve likely seen the below warning while browsing a website before.
Website owners should prioritize WordPress security since Google mainly blocklists sites for malware and phishing. Use Google’s Safe Browsing tool to check your safety report.
Your WordPress website may become vulnerable to hackers who can create a backdoor to your file system. This involves replacing your website’s legitimate code and redirecting traffic to spammy locations. This can result in your website being infected, misbehaving, and getting blocklisted from search engine results. To prevent a sudden drop in website visitors, continue vigilance and apply a robust security plugin to avert the threat beforehand.
2. Your Website Is Defaced or Vandalized
If your website’s homepage has been defaced, it indicates that it has been hacked. While most hacking attempts aim to remain unnoticed, some hackers deface websites to make themselves known.
Taking immediate action is crucial when your website’s homepage or layout has been altered. It could be hackers injecting malicious content to steal personal info, redirect visitors, or spread malware via drive-by attacks using malware droppers.

Website Defacement: A Potential Sign of Ransomware
Furthermore, a defaced website could be one of the most apparent signs of an upcoming untoward incident. Because as the next step, hackers may replace your homepage with their message or demand money to restore your website. This operates similarly to ransomware, a cyber attack responsible for 10% of data breaches in 2022.
Additionally, Sophos, a leading cybersecurity service provider, has published its annual State of Ransomware 2023 report, revealing that 76% of surveyed organizations fell prey to ransomware attacks that resulted in data being encrypted. The study further highlights that organizations that opted to pay the ransom wound up incurring double the recovery costs ($750,000) compared to those who utilized backups to restore their data ($375,000).
Consider seeking professional assistance to rectify the homepage vandalization issue to avert falling prey to such an attack.
3. Your Website Is Slow or Experiences Unresponsive Website Performance
The F5 2023 DDoS Attack Trends report highlights a concerning surge of 165% in attacks aimed at exploiting vulnerabilities and consuming resources of applications and services.
Distributed denial of service (DDoS) attacks can target any website, service, or network. DDoS attacks often involve controlling networks of hacked computers and servers, creating what’s known as a botnet. Also, fake IP addresses are sometimes used to mask the origins of attacks.
While it is possible to check your server logs and block problematic IPs, this may not solve the issue if there are multiple hackers, or if they use a proxy server to mask their true IP addresses.
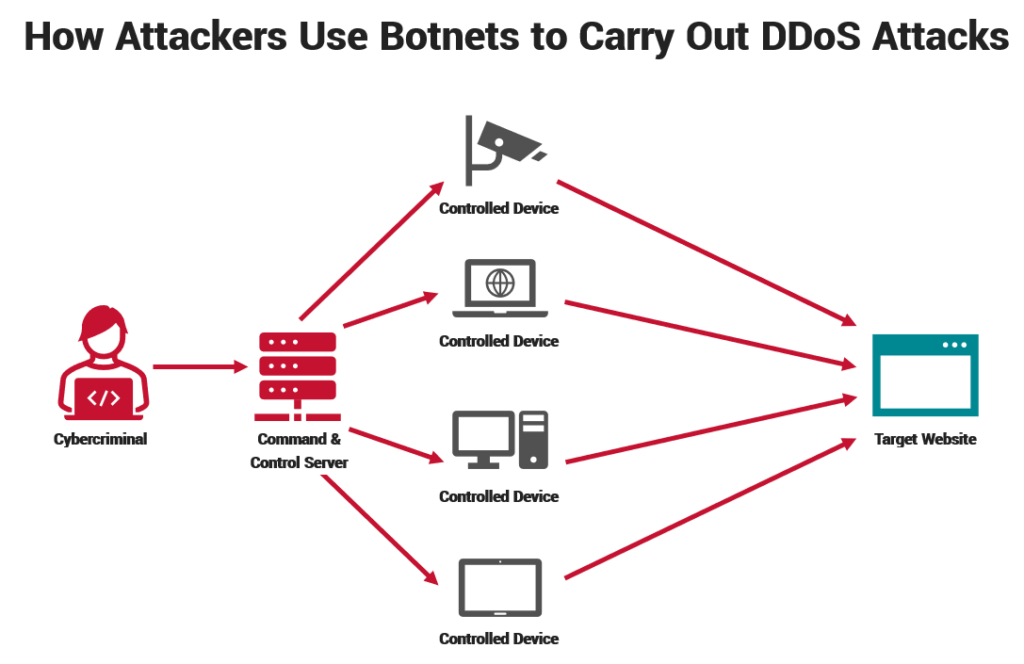
The effects of DDoS can range from slowing down your website to rendering it wholly unresponsive and unavailable. Hence, if you suspect your WordPress site is slow or unresponsive, it could be a sign of a DDoS attack requiring immediate mitigation procedures.
4. There Are Backdoors on Your Site with Possible Data Injections or Malware Links
If a website is hacked, the perpetrator commonly establishes a backdoor, which serves as a hidden entry point for subsequent unauthorized access. This backdoor enables the attacker to reenter the website without raising suspicion. Hackers frequently mask these backdoors to conceal their illicit activities as seemingly harmless elements, such as themes or plugins.
However, backdoors can be used to carry out both server-side and client-side data injection attacks.
Also, data injection is among the most common signs if you suspect your WordPress site has been hacked. It is now ranked third on OWASP’s top 10 web application security risks list, with around 94% of tested apps showing some vulnerability. This category has the second-highest occurrence of application issues, and 33 types of common weaknesses are mapped to it.
- Server-side data injection attacks: In server-side attacks, a backdoor is planted in a server application or system to inject malicious code or commands. This attempt can lead to SQL injection or remote code execution attacks, allowing unauthorized access to the server.
It exploits vulnerabilities in components, such as web applications or databases, to inject malicious data or commands.
Vulnerability Checks:
- Implementing proper input validation and sanitization techniques in server-side code can prevent the execution of unauthorized commands.
- Regularly scan your server for vulnerabilities and suspicious activity.
- This can be done using specialized tools and software that can identify and flag any unusual behavior or code injection attempts.
- It is also essential to keep your server software updated with the latest security patches. Limit access to sensitive data and applications to authorized users only.
- Client-side data injection attacks: In client-side attacks, a backdoor is embedded in a web page, plugin, or application, triggering when a user interacts with it. This crack can result in cross-site scripting (XSS) or code injection through malicious downloads, leading to data theft or unauthorized access.
Vulnerability Checks:
- Hackers often target vulnerabilities in client-side components like web browsers to inject malicious data or scripts that execute within the user’s browser.
- In some cases, spammy or malicious links may be added to a website through backdoors, which can appear anywhere on the site, including the footer section.
- It’s important to note that simply deleting these links may not be enough to prevent them from reappearing.
- To effectively eliminate them, you must locate and fix the backdoor that the hackers used to inject the data.
Hacked Metatags Backdoor Attacks
Backdoor attacks also involve hackers exploiting website vulnerabilities to inject malicious code that alters visible meta tags meant for search engines, which may result in incorrect titles and meta descriptions in Google search results. Robust security measures, regular monitoring, and aftermath cleansing can mitigate the risks of hijacked search results attacks.
5. Unknown Pop-Ups or “Malvertising” Codes Are Present on the Site
According to AV-Test, there are approximately 12 million new malware variants per month, with 390,000 malicious programs being detected on a daily basis. So, when you notice spammy ads or unexpected pop-up nuisances on your website, it’s a sign that malware may have hit your site.
Hackers use malvertising tactics to redirect users to their own spammy sites to generate income. Failure to promptly address malvertising or malware ads can sometimes result in complete chaos and significant business losses, as these ads could be challenging to detect. The ads are usually visible to new visitors who arrive at your site from a search engine but not to logged-in users or those who access your site directly.
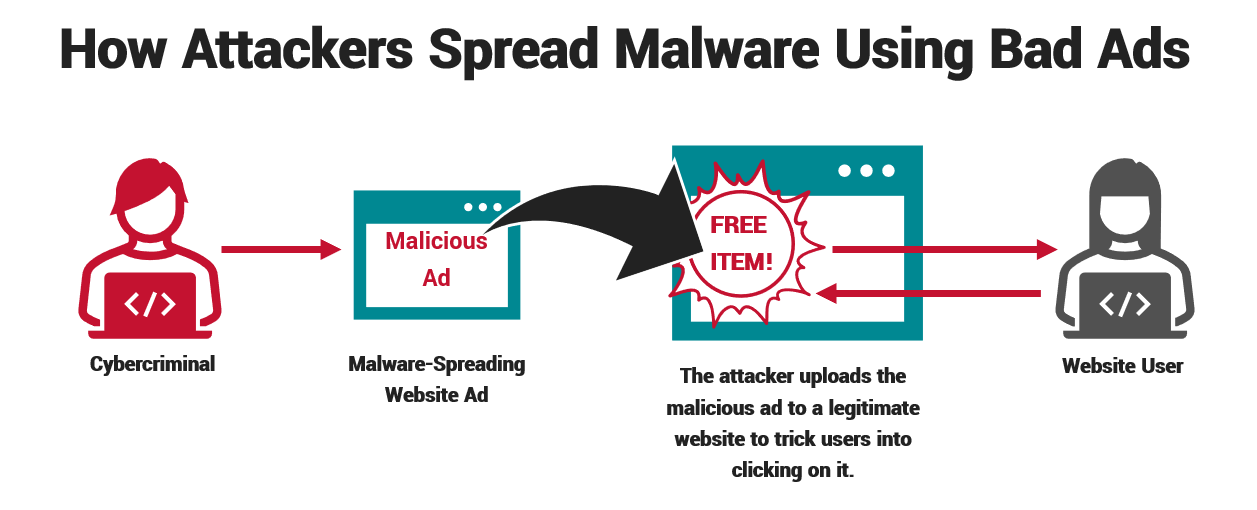
If your WordPress site is running slow or unresponsive and filled with pop-ups and sidebar ads, it requires immediate attention. The hack occurs because automated attacks target weakly protected themes or insecure plugins. When ads start to appear, they lead visitors from your site to spam websites that can harm your website, traffic, and reputation. Also, pop-under ads are incredibly sneaky as they open in a new window and can go unnoticed by your visitors.
Acting immediately if you receive a malvertising warning on your site is essential. Hackers gain access to your server through backdoors they install, making it vital to submit a reconsideration request and ask Google to review your site once again once it is malware-free. You can also rectify the issue and protect your website from further harm by installing a WordPress plugin to help guard your site against malware ads.
6. You Face WP-Admin Failed Logins or See Unfamiliar User Accounts on Your Dashboard
If, as an Admin, you can’t access your WordPress site, it could mean that hackers breached your security. Once they gain access, they can use it to erase your account or alter your login credentials.
It is vital to create strong passwords and refrain from using common usernames such as “admin,” “administrator,” “test,” or “root.”
The Threat of Bad Bots and Spam Accounts
A 2023 Imperva Bad Bot Report says around 30% of automated internet traffic comes from bad bots, which are programmed to carry out malicious activities like content scraping, DDoS attacks, and brute force attacks.
Bad bots pose a severe threat to website owners as they can steal sensitive data, consume server resources, and affect website performance. Additionally, bots create spam accounts that harm your reputation and redirect users to harmful websites.
Suspicious accounts with admin roles could mean your site is hacked. Regularly check your WordPress dashboard for spam accounts, especially if your site allows user registration. In addition, spam comments can harm your site’s reputation, clutter your database, and expose users to unsafe websites. So even if the bots are unable to break your WordPress core files, they’re a problem to tackle.
Unfamiliar SFTP and FTP User Accounts
To keep your website secure, pay attention to your secure shell file transfer protocol (SFTP) or FTP accounts. These are the protocols that provide access to your website’s back-end files and folders. Keep an eye out for any new or unknown accounts because it may indicate that your website has been hacked.
Your hosting account will usually have a single user account automatically created. If you notice additional or unfamiliar accounts associated with your site, remove them immediately, and change passwords on your known legitimate accounts.
7. You Detect Unknown Files and Suspicious Scripts in Your Server Logs
Malicious files and scripts can be hard to detect as they are often disguised as legitimate WordPress files and concealed in the /wp-content/ folder. Deleting them may be a temporary solution, as they can reappear.
Therefore, it is crucial to regularly check your file and directory structure for any suspicious files and take measures to strengthen your security. One such example is updating your WordPress and plugins and using strong passwords.
A security tool like Sitelock can help you detect unknown files or scripts on your server. You can operate an SFTP client to connect to your WordPress site to locate them.

Don’t leave your website’s security to chance. Take action now and sign up for SiteLock to safeguard your online presence. With SiteLock, you’ll get the peace of mind you need to focus on growing your business.
Server Logs Detect Suspicious Activity
Your server logs track important internet traffic and error information. Check them through your cPanel dashboard to identify suspicious activity. For example:
- Access logs show who visited your site, when, and what they accessed and how they did so;
- Error logs, as their names imply, reveal issues with or modifications to your WordPress files.
Regularly review records and block unknown IP addresses to prevent unauthorized access. Make sure your hosting provider offers an easily accessible menu for this feature.
Diagnosing WordPress Site Loading Glitches
Examine the error message for clues to diagnose a website that is not loading. Common WordPress errors such as HTTP 500, 502, and 503 can stem from server-side issues, traffic spikes, attacks, or faulty plugins. Other errors like 401, 403, or Connection Refused may indicate password changes or other authentication issues, file permissions, or potential hacking attempts.
8. Your WordPress Emails are Not Going Through, Signaling Potentially Compromised Servers
- In a startling disclosure, 300,497 phishing attacks were reported to the FBI in 2022.
- While IBM statistics show phishing costs corporations an average of $4.91 million each.
Hackers can infiltrate your website and install malicious code that leads to phishing attacks (i.e., sending spammy emails from your domain). Consequently, your site may be marked as fraudulent, preventing you from sending or receiving emails. If you can’t send or receive WordPress emails, it could suggest problems with your site’s mail servers, which may include hacking or improper configuration.
Compromised servers are a favorite tool of cyber attackers for sending spam. Many WordPress hosting companies offer free email accounts, and WordPress site owners often use their host’s mail servers to send WordPress emails. Thus, loosely secured servers constitute a significant cause of security breaches.
9. You Get Unauthorized Charges on Your eCommerce Gateway Suggesting a Data Breach
Visa’s Chief Risk Officer, Paul Fabara, shared with Axios that the world saw a 20-30% surge in e-commerce “friendly fraud” cases in 2022. This increase was attributed to the rising number of consumers reporting valid transactions as fraudulent due to information theft or deceptive purchases.
If you’re operating an eCommerce site using a plugin and receive multiple customer complaints about unauthorized charges, it may indicate that a data breach has occurred. For example, this could occur if a malicious party accessed your website or payment gateway.
Ecommerce plugins are expected to adhere to Payment Card Industry Data Security Standards (PCI DSS) security practices and shouldn’t store your website’s credit card numbers or security codes. However, customer details like names, addresses, and emails are still vulnerable if your database is compromised. Hackers could exploit this information to commit identity theft or unauthorized charges on stolen credit cards.
As a responsible eCommerce business owner, it’s crucial to prioritize the security of your customer’s personal and financial information by implementing robust security measures and regularly monitoring your systems for any suspicious activity.
Even if you opt for secure payment processors, it is still on your part to remain aware of PCI-DSS, tokenization, and other relevant data security and privacy regulations compliance to be on the safe side. So, proactively implement security measures to build trust and prevent breaches. Remember, customer security is your responsibility.
10. There are Unexpected Modifications in Your Core WordPress Files
The PHP and related source files that make up the primary functions of WordPress are called WordPress core files. These files should not be modified in any way, as doing so may cause incompatibilities and other issues regarding your WordPress site’s operations.
When hackers gain unauthorized access to your WordPress site, they can potentially bring modifications to your core WordPress files, such as replacing or creating new files, leading to security breaches. To confirm the integrity and security of your WordPress core files, use WordPress security plugins, such as SiteLock security, to identify any suspicious file modifications and monitor the overall health of your core WordPress files.
Inspecting your WordPress files and folders for unusual or malicious scripts is helpful but time-consuming. Stay vigilant and save valuable time by using automated website scanning tools.
Learn More About SiteLock’s Daily Security ScansFinal Thoughts on Checking Your WordPress Site for Hacks
To stay vigilant against hacking attempts and take the necessary steps to secure your WordPress website, opting for a reliable plugin is always advisable. An automated plugin will set up security features like software alerts, file permissions, and firewall solutions on your website to deter hacks.
For a complete, hassle-free WordPress hack mitigation, we recommend you SiteLock 24/7 monitoring and cleanup services.
Additionally, we have resources for understanding encryption with SSL certificates and offer business phone services for SMEs and large-scale businesses.
Remember, your website represents your online identity; keeping it safe from potential threats is essential.
So, stay vigilant, stay safe, and keep your website thriving.