Public Key and Private Key Pair: How it Works
Let’s have a look at the role played by the Public–Private Key Pair in Today’s Cryptography
Public Key and Private Key pair is the core component of public key cryptography. These keys are responsible for carrying out encryption and decryption. Both keys are co-related to each other. That means that one private key can only have one public key and vice versa. To put this in even more simple words, they both come in pairs – a private/public key will only work with the public/private key associated with it.
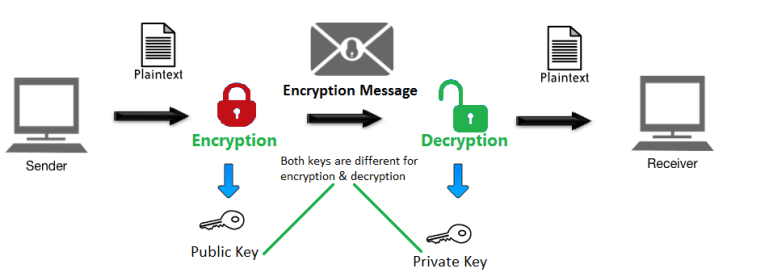
This key pair is used in asymmetric encryption, the encryption system used in SSL/TLS certificates as well as in Bitcoin and other such cryptocurrencies.
In this system, the data is encrypted using public key and decrypted through the private key. As implied in the name itself, a public key is publicly accessible. These public keys can be accessed through publicly available directories.
This is what the public key for Google.com looks like:
04 bb 0d 2f 9a dd 79 e5 6f f2 fd a4 40 38 ba 7e 9a 66 f5 e7 7b 06 32 90 51 f6 4f 56 2d 0f ab 15 2a 17 41 79 99 1a 9f 49 09 3f 9c 85 92 52 9c a0 61 d4 2d bd 3a 4d 4d 21 29 a9 91 98 1d c4 b8 c9 5d
So, when you go to Google.com and type in your search query in the box, your search query will be encrypted with this public key, and then it gets sent to Google’s web server, where Google’s private key is responsible for carrying out the decryption. Keep in mind that this entire process is much more complicated than this. We’ve tried putting it as simply as we could so that you could understand it better. If you want to dig in deep, have a look at the SSL handshake portion of this post.
When you issue an SSL certificate for your site, a private key is generated. Needless to say, this key is supposed to be kept private. If compromised, an attacker could impersonate your server or your crypto wallet, and the consequences could be catastrophic. That’s why storing it securely is absolutely pivotal from the security point of view.
Private Key Storage: Best Practices
We cannot stress enough the significance of the secrecy of your private key. To ensure that your private key doesn’t get compromised in any way, you must tighten its security. Here are the best practices that will help you do it:
-
Store it in a hardware token
No matter how much technologies change, some things will always be better the way they are. A secure hardware token is one such example. A hacker can break through your system if it’s stored on your systems, but it’s tough to get hold of a hardware token or a smart card that is stored locally—as in, not online at all. And even if one manages to, he/she will have to crack the password, which is mightily difficult.
The thing that you need to keep in mind while using a hardware token is that you should keep it disconnected to your systems. Otherwise, there’s no point in it.
-
Only grant access to authorized people
The private key is called “private” for a reason. By limiting the user access, you also limit the potential risks coming along with it. You should never grant access over remote connection as well.
-
Use Key Stores
Some browsers and operating systems allow their users to store cryptographic keys in secure environments that are called ‘key stores.’ Stores such as Windows Certificate Store and Mac OS Keychain are the best examples of it. These stores are easily customizable and can be protected using strong encryption.
-
Multi-factor Authentication
If you have stored your private key on your system and given access to trusted people, you should always implement multi-factor authentication; it’s the new norm these days.
-
Backup the private key
At the end of the day, no matter how much we surround ourselves with machines; we’ll always be humans (at least a part of us will be). And as humans, we’re bound to make mistakes. That’s why backing your private key is always a good idea as long as it’s backed up securely.
We hope this post has given you a clear idea about Public and Private Key, and the role played by them in keeping our data secure.


