What is S/MIME? How does it work? Do I need S/MIME?
Here’s everything you need to know about S/MIME certificates
S/MIME, the acronym of Secure/Multipurpose Internet Mail Extensions, is a universal web standard defined by the IETF. S/MIME is employed to encrypt MIME data—emails in simple terms. Initially developed by RSA Data Security, it’s been made a standard by the IETF and has been defined in many of its documents.
S/MIME, based on Public Key Infrastructure or Asymmetric Encryption, facilitates email security by virtue of encryption, authentication, and integrity. In other words, it allows you to digitally sign your emails so that only the intended recipient can see the message and he/she also gets to know that the email really came from you. While the email is on its way, the encryption takes care of its integrity as it doesn’t allow an unauthorized third party to intercept and tamper with the data.
![]()
Protect your email data and communication through Email Signing or S/MIME Certificate. Buy directly from ComodoSSLStore.com and get your Personal Authentication certificate issued within minutes for as little as $12.95 per year.
This way, S/MIME goes a step beyond email server encryption. Installing a digital certificate an email server is always a good idea as it thwarts any attempts at man-in-the-middle (MiTM) attacks. However, this is not enough. Even if your email server has been encrypted, it still cannot stop a perpetrator from stealing emails from your inbox as the emails are stored unencrypted on the servers. Also, it doesn’t protect when your emails are in transit from another server.
Both of these downsides can be eliminated using an S/MIME (client) certificate. Yes, there’s a certificate for that. To implement S/MIME, you must install an S/MIME certificate—also known as “client certificate.” As they work on the principles of public key infrastructure (PKI), what they do is pretty similar to SSL certificates. The only key difference is that these certs are installed on clients while SSL/TLS certs are implemented on servers.
Benefits of S/MIME Certificates
- No repudiation: The sender cannot deny having sent the email and its contents. A digital signature is proof that the email has come from the signer’s email client.
- Protection from in-transit email corruption: No cybercriminal can insert any sort of malicious software such as viruses, spyware, trojan horses, computer worms, rootkit, etc. while the email is in transit.
- Protection from email spoofing: Digital signature protects the email recipients from email spoofing. No one can impersonate the digital signature of the company’s official staff members. So, no one can trick the recipients by sending spoofed emails impersonating the business’s authentic emails. (Or if they try, they’ll be lacking a signature.)
- Warns recipients: If someone has tampered with the email or digital signature, it immediately alerts the recipients about the risk. So, the recipients know that something is fishy about the email and can protect themselves from becoming victims of the cyberattack before it’s too late.
- Protects business’s reputation: If the clients/customers get an email containing viruses or malicious links from the organization’s official email addresses, it can instantly tarnish the business’s reputation. With S/MIME certificates, no email tampering is possible. Hence, it helps to protect a business’s reputation to a great extent.
- Prevents data leaks: An S/MIME certificate protects data from eavesdropping and leakage. The company’s confidential communications with internal and external stakeholders remain secured due to the encryption functionality.
- Ensures compliance. Multiple laws require encryption of sensitive information, including GDPR, HIPAA, and PCI-DSS. Encrypting emails is one important tactic needed to stay compliant.
Bonus Point: If you buy Comodo’s S/MIME certificate, called CPAC (Comodo Personal Authentication Certificate) it can not only be deployed on emails but also be used to sign and encrypt documents and files! Plus, you can implement it for authentication at the organization level to get the benefit of two-factor authentication and client authentication, too.
Types of S/MIME Certificates
As you read above, Comodo’s S/MIME certificates are known as the Comodo Personal Authentication Certificate (CPAC). They are available in three categories. All these certificates offer the same email signing, document signing, encryption, and client authentication features. But each of them requires a different validation process and displays different authentication details on the certificate.
CPAC Basic: You need to go through the domain validation process to prove your domain ownership. You just need to click on the verification link that you will receive on the email address you have provided. After successful deployment, the certificate will show your [email protected] as your digital signature on the certificate. It provides assurance to all your recipients that the email has really come from you.
CPAC Pro: To get a CPAC Pro issued, you must go through the domain validation and Identity verification process. (The identity verification process is the same as that of code signing certificates). This certificate will show your first name, last name, and the email address as your digital signature in all your outgoing emails.
CPAC Enterprise: This one requires the highest level of validation. You need to go through domain validation + individual validation + organization validation. The organization validation process has four parts, which include organization authentication, locality presence check, telephone verification, and final verification call. After successful verification, you would be rewarded with an enhanced digital signature. The certificate will contain:
- [email protected]
- First Name, Last Name
- Company Name
- Company Address
Which clients support S/MIME?
These are some of the many desktop and mobile email clients that support email encryption certificates:
- Apple Mail
- CipherMail
- Gmail (paid version)
- IBM Notes
- iPhone iOS Mail
- MailMate
- Microsoft Outlook and Outlook on the Web
- Mozilla Thunderbird
How to Digitally Sign Emails in Outlook With an S/MIME Certificate
Step 1: Buy an S/MIME certificate. If you get it from comodosslstore.com, you will get as much as a 78% discount on the email signing certificate.
Step 2: Install the certificate in Outlook .
Step 3: Now, click on the File and go to the Options.
Step 4: The Outlook Options window will pop-up. Click on the Trust Center from the left side menu. Go to Trust Center Settings.
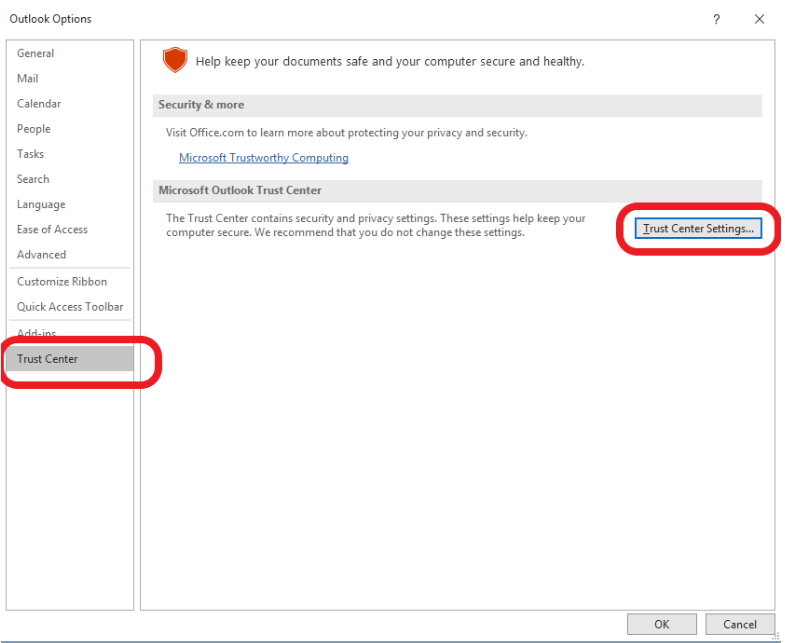
Step 5: Locate the Email Security tab. Under the Encrypted Mail section, carefully read all four options. Among them, to add the digital signature to all the outgoing emails, you need to select Add digital signature to outgoing messages.
Select Send clear text signed message when sending signed messages to option if you want to let recipients without an S/MIME certificate read the email content.
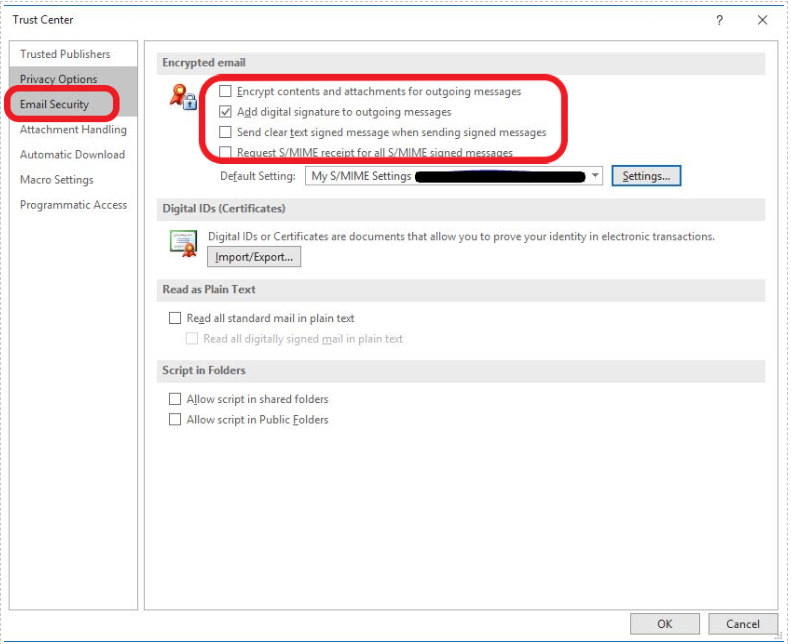
Step 6: Click, OK.
Congratulations! Now, when you send emails, the digital signature will automatically be attached to all your outgoing emails. As shown in the screenshot below, the small ribbon icon on the email represents your digital signature. By clicking on it, the recipients can see a security dialogue authenticating your (sender’s) identity.
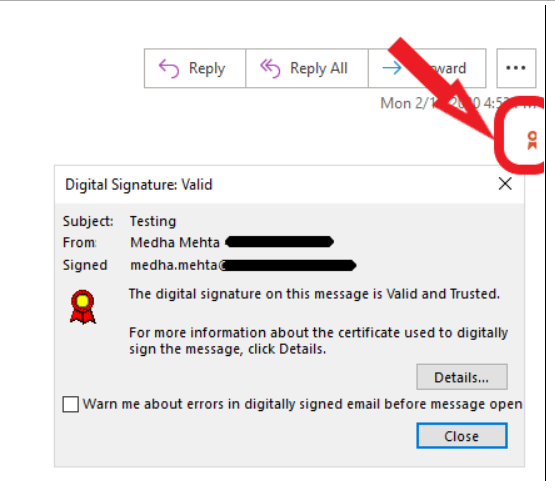
How does S/MIME (Client) certificate work?
As we saw earlier, S/MIME certs are based on asymmetric encryption. That’s why they involve two distinct keys – a public key and a private key. Keep in mind that a public key and private key come in a pair, one public key can only have one private key and vice versa. This is because they’re mathematically related to each other, the public key is actually derived from the private key.
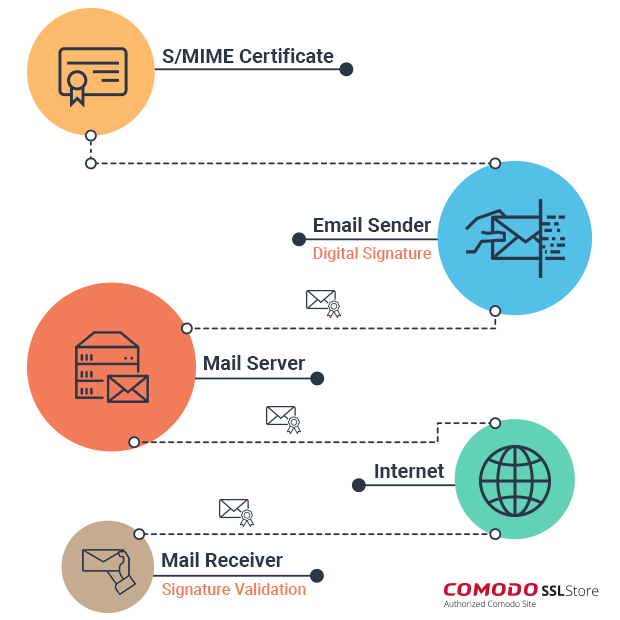
While using an S/MIME certificate, a sender sends an email by encrypting it through recipient’s public key. On the other side, the recipient decrypts the email using the private key he/she has. There’s no scope for someone else to come in between and see or tamper with the email as it’s in an encrypted format.
In simple terms, this entire process is called ‘signing.’ You might have heard some security experts talk about signing emails. Well, this is what signing your email means.
Signing emails, as you can see, removes two significant roadblocks in email security. First, it takes away the likelihood of a 3rd party intervention while the email is in transit. This will work even if you haven’t encrypted your server (but don’t use this as an excuse, you still need to encrypt your server). Another thing this does is provides authentication to the user as the signature of the sender is attached to every email.
As you can see, it’s a win-win for everyone—except the hackers.
All of this works splendidly as long as the private key isn’t compromised. If it gets compromised, all the floodgates open up. Remember, it’s your private key, it’s supposed to be private. If you want to know about best practices to store your private keys, here’s the perfect article for you.
We hope we’ve been able to give you a bright idea about S/MIME and S/MIME certificates.
Save Up to 75% On
Comodo SSL Certificates
Tip: You can typically save a significant amount by buying your SSL certificate direct instead of through your web hosting company. We sell all Comodo SSL certificates at up to 75% off.


 (17 votes, average: 4.18 out of 5)
(17 votes, average: 4.18 out of 5)