SSL Asterisk in Action: A Look at Wildcard Certificate Examples
What does a wildcard SSL certificate look like when in use? We’ll examine examples of basic wildcard and multi-domain wildcard certificates
Whether you’re looking to secure a single domain and all of its first-level subdomains or upwards of 250 root domains with its single-level subdomains, there’s a wildcard certificate example that would work for that purpose.
- A standard wildcard SSL certificate allows you to enable HTTPS and attach your organization’s digital identity to a particular domain and its first-level subdomains.
- A multi-domain wildcard SSL certificate takes these subdomain-securing capabilities and rockets them to a whole new level by also allowing you to secure multiple root domains and multiple subdomain levels simultaneously.
As with anything else in life, there are advantages and disadvantages to each type of wildcard certificate example. But what does a multi-domain wildcard SSL certificate look like? And how can you tell whether a website is using one?
Wildcard Certificate Example #1: A Basic DV Wildcard
A standard wildcard SSL/TLS certificate is an X.509 SSL/TLS certificate that secures a single root domain and unlimited subdomains on a single level (e.g., email.itsatest.site, login.itsatest.site, and dev.itsatest.site). It uses an asterisk (*), or what’s known as a wildcard character, to specify the wildcard subdomain level.
It’s a flexible and cost-effective option for businesses that have a single domain but many subdomains to secure. For example, the wildcard version of the domain (*.itsatest.site) covers your root domain (itsatest.site) and all of your first-level subdomains, such as:
- gondor.itsatest.site
- travel.itsatest.site
- minas-tirith.itsatest.site
Here’s what a wildcard certificate example looks like in the wild, as seen on millerharris.com.au:
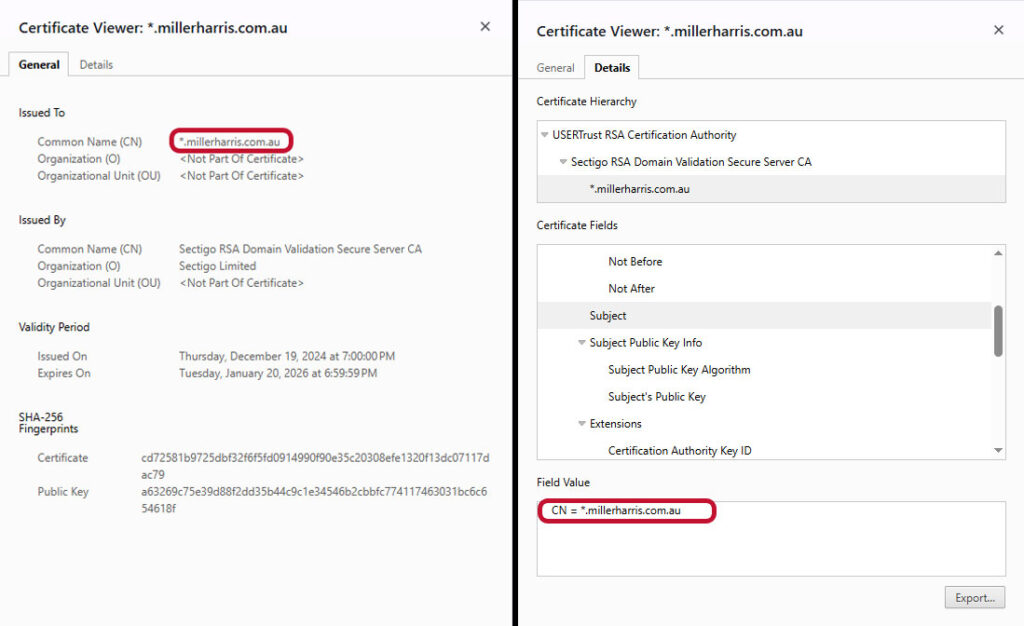
But what if you want to use a single standard wildcard certificate to secure multiple levels of subdomains on a single domain simultaneously? Or, what if you want to secure multiple subdomain levels on multiple separate domains? Then this isn’t the right certificate for you.
Let’s consider the first scenario. Since you can’t secure multiple subdomain levels using a single standard wildcard certificate, it means you’d have to use multiple certificates, with each covering a single subdomain level:
- one certificate to cover *.itsatest.site (first level)
- a second certificate to cover *.news.itsatest.site (second level)
- a third certificate to cover*.blog.news.itsatest.site (third level)
The good news is that there is another type of wildcard that will fit the bill for the second scenario…

Comodo Wildcard Certificates – Save Up To 72%
Save a bunch when you buy direct. Get a Comodo Wildcard Certificate for less than $80 per year.
Compare Wildcard Certificates
Wildcard Certificate Example #2: A Multi-Domain Wildcard
A multi-domain wildcard SSL/TLS certificate is a more robust option for businesses that have a plethora of single-level subdomains to secure across multiple domains or IP addresses. For example, take a look at the individual wildcard domains secured by the following multi-domain wildcard SSL certificate for nextblue.ca:
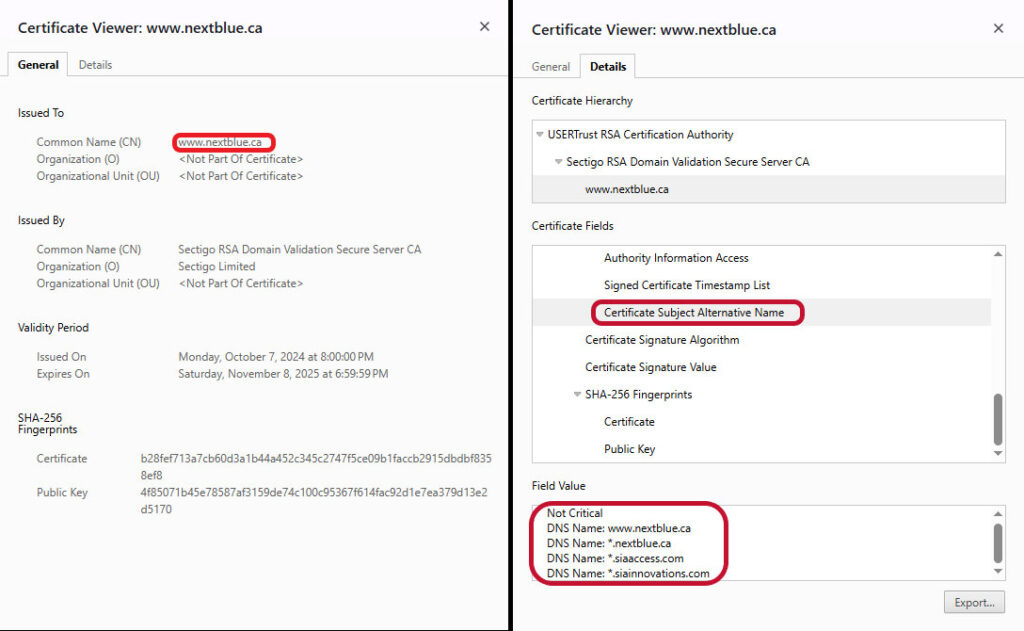
In this case, this certificate secures three wildcard domains and the WWW version of the root domain. It also displays a wealth of other information, including:
- Common Name (CN) that the certificate was issued for
- Name of the issuing certification authority (Sectigo) and the root it chains back to
- The leaf certificate’s hierarchy, which shows what root the endpoint certificate ultimately chains back to
- The certificate’s validity period (i.e., its issuance and expiration dates)
Save Up to 58% on Wildcard SAN Certificates
Tip: You can typically save a significant amount by buying your SSL certificate direct instead of through your web hosting company. We sell all Wildcard SAN certificates at up to 58% off.
Shop for Wildcard SAN CertificateSo, thinking back to the second scenario we described — the one where you want to secure multiple levels of subdomains across several root domains. How would you solve it? You could use a multi-domain/SAN wildcard certificate to:
- secure the root domain (with the CN specified as a FQDN), and
- secure additional alternate domain names and multiple levels of subdomains (all of which would have to be specified as separate SANs).
Great! Now we know how these two wildcard certificate examples work. But what do they actually look like when deployed in the wild?
How to Tell Whether a Site Uses a Wildcard SSL/TLS Certificate
We’ve shown you what wildcard and multi-domain wildcard SSL certificates look like. But when push comes to shove, do you know how to differentiate wildcards from other types of SSL/TLS certificates?
Moreover, how can you tell the difference between a standard (single domain) wildcard and a multi-domain wildcard SSL/TLS certificate?
Check Out the Certificate’s Common Name for the Tell-Tale Asterisk (*)
The common name field is a big clue — if the Common Name domain starts with an asterisk (e.g., *.comodosslstore.com), this indicates the site is using a standard single-domain wildcard SSL/TLS certificate.
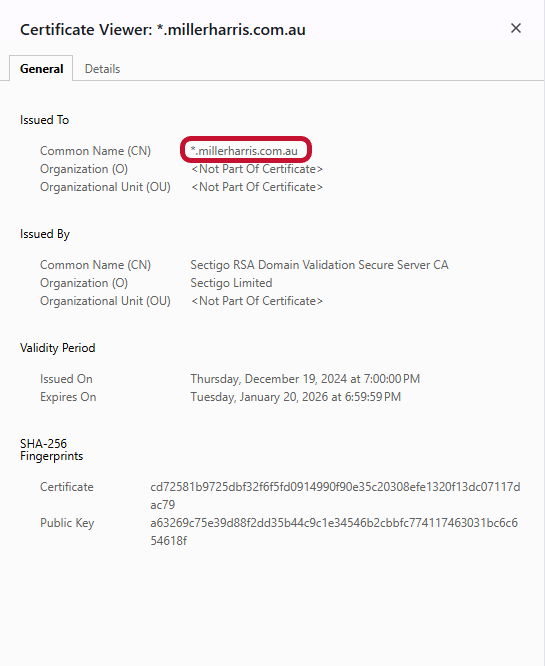
This differs from a multi-domain wildcard SSL/TLS certificate, which must use a fully qualified domain name (FQDN), either the WWW or the non-WWW version, as the CN and lists wildcard domains and alternate root domains in the SAN field.
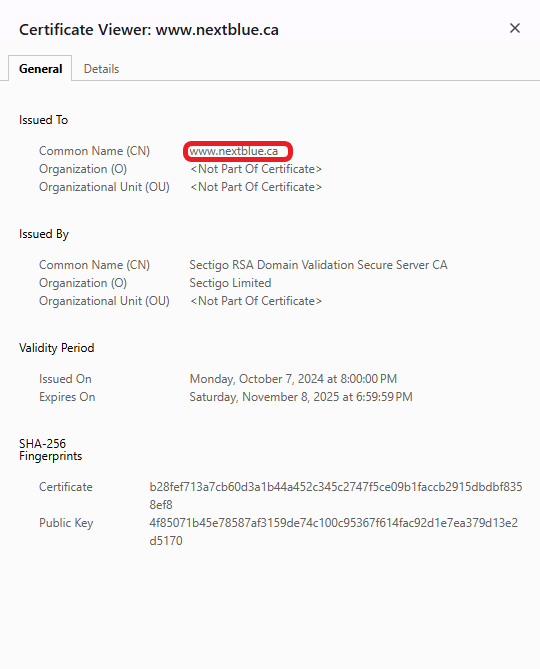
Inspect the Certificate Subject Alternative Name Field
The SAN field is a dead giveaway for identifying a multi-domain SSL/TLS certificate. For example, when you see multiple root domains and subdomains listed as subject alternative names, it indicates that the certificate is a multi-domain wildcard.
Want to learn more about the differences between basic wildcards and multi-domain wildcard SSL/TLS certificates? Check out our related resource.

